HALOCK Security Labs | Reasonable Security on Twitter: "Only a few days left to register for the CIS RAM webinar. Learn how to establish 'Duty of Care' for Cybersecurity April 30, 2018 -

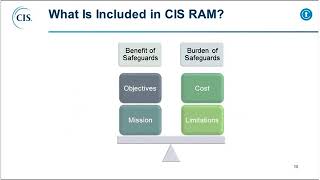
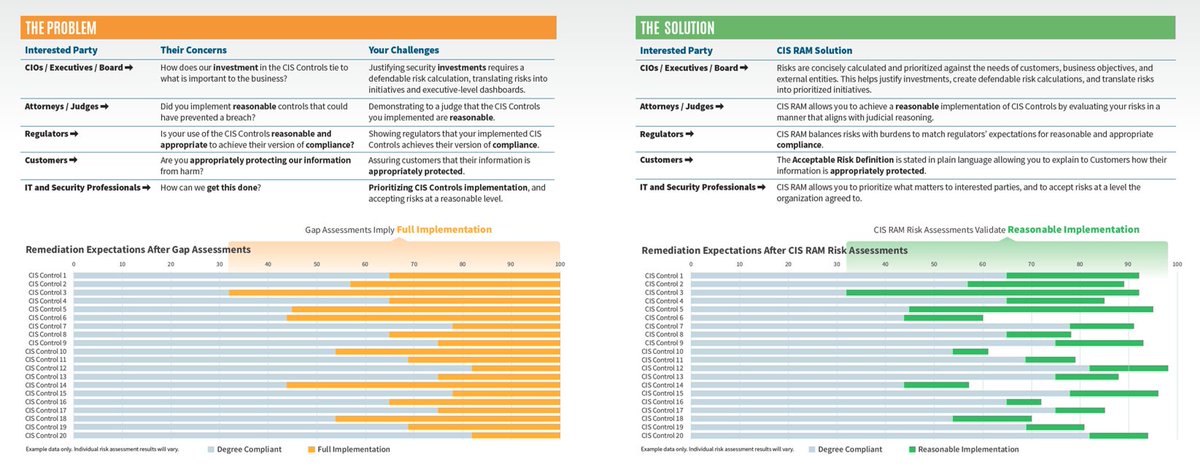
HALOCK Security Labs - CIS RAM Puts the CIS Controls™ into Action Developed by HALOCK Security Labs in partnership with CIS, CIS RAM provides three separate security approaches to support different levels