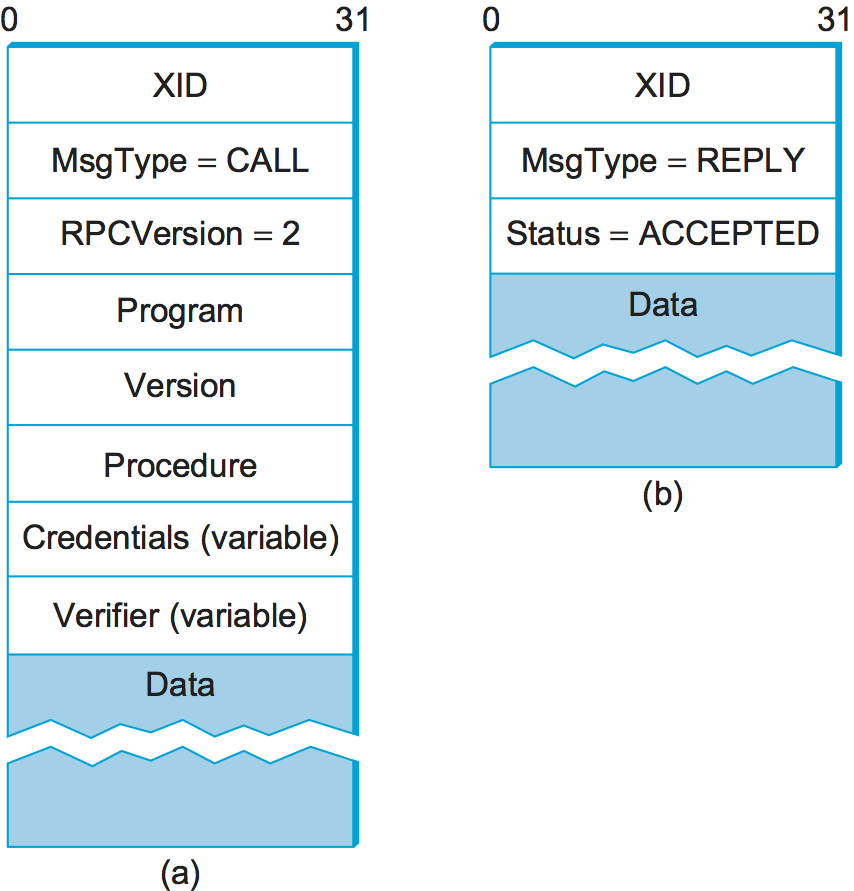
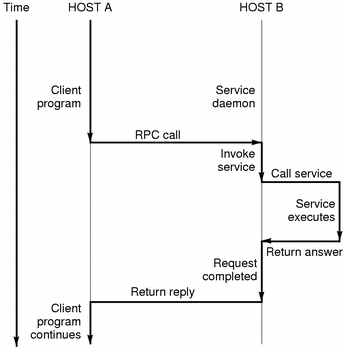
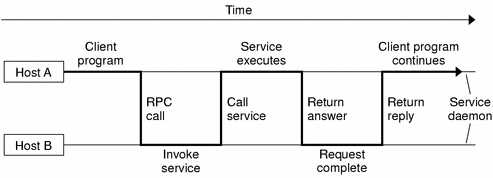
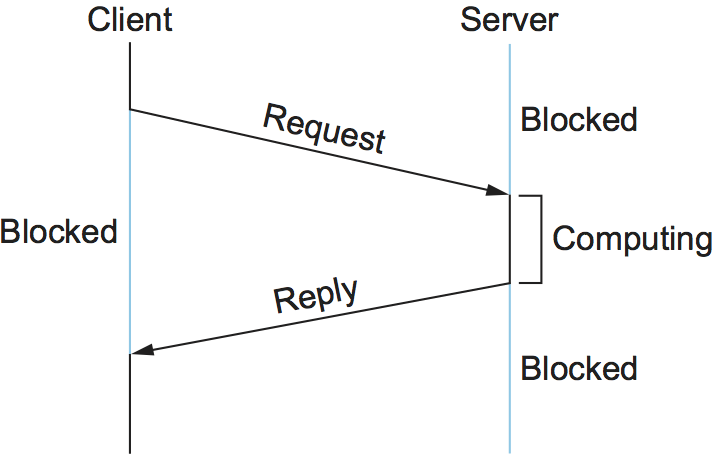
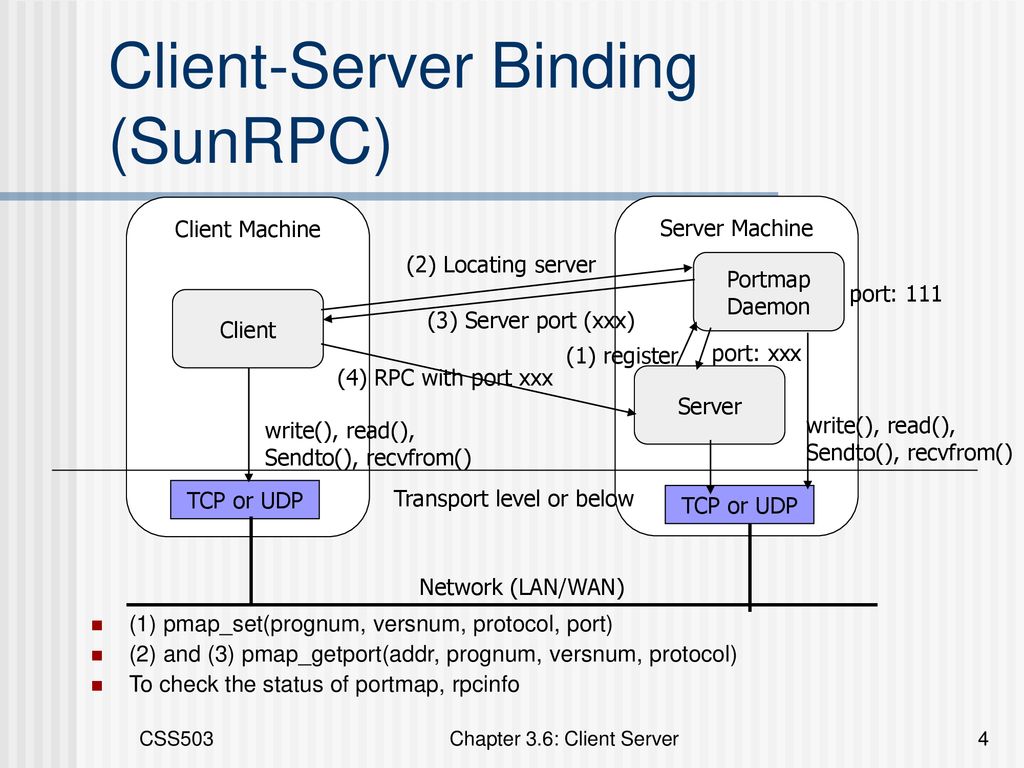
![Firepower Management Center Configuration Guide, Version 6.1 - Application Layer Preprocessors [Cisco Secure Firewall Management Center] - Cisco Firepower Management Center Configuration Guide, Version 6.1 - Application Layer Preprocessors [Cisco Secure Firewall Management Center] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/370001-380000/371001-372000/371940.jpg)
Firepower Management Center Configuration Guide, Version 6.1 - Application Layer Preprocessors [Cisco Secure Firewall Management Center] - Cisco

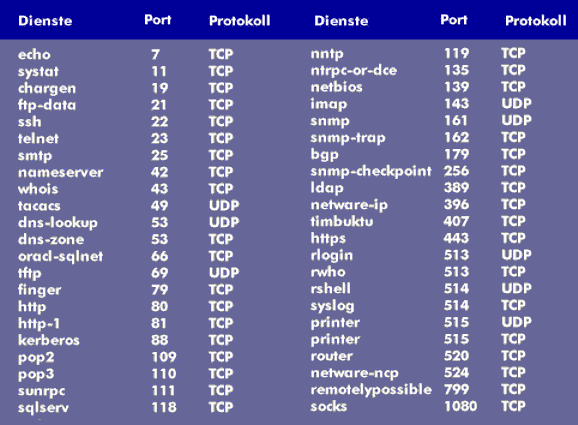
Solved: what port number range should be opened in the direction from nfs server to nfs client side? - NetApp Community
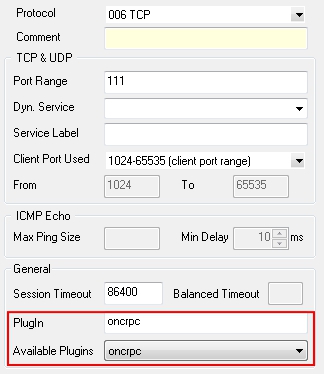
![Firepower Management Center Configuration Guide, Version 6.1 - Application Layer Preprocessors [Cisco Secure Firewall Management Center] - Cisco Firepower Management Center Configuration Guide, Version 6.1 - Application Layer Preprocessors [Cisco Secure Firewall Management Center] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/370001-380000/371001-372000/371939.jpg)