Fundamental Mechanisms of Regulated Cell Death and Implications for Heart Disease | Physiological Reviews
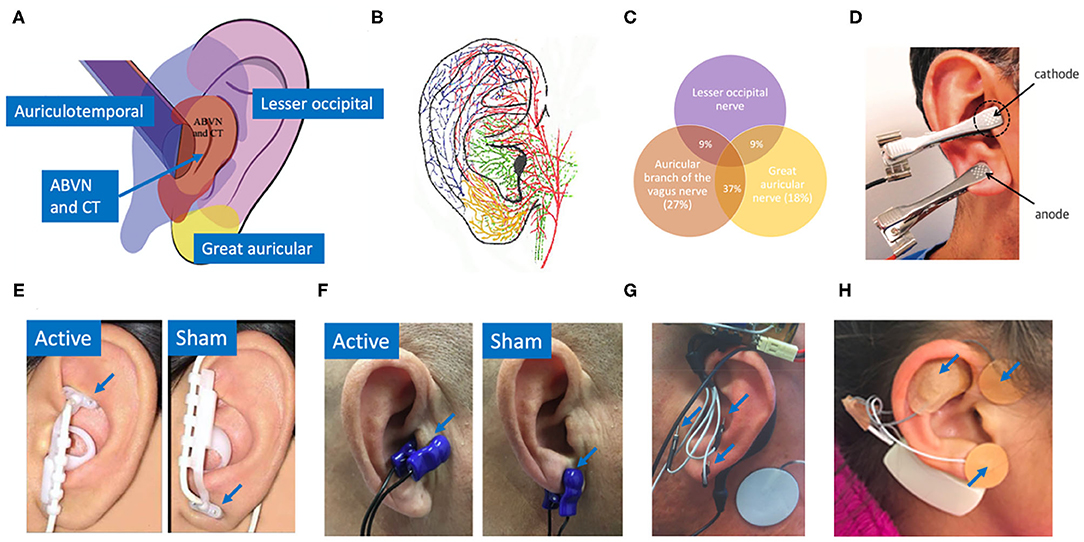
Frontiers | Auricular Vagus Neuromodulation—A Systematic Review on Quality of Evidence and Clinical Effects
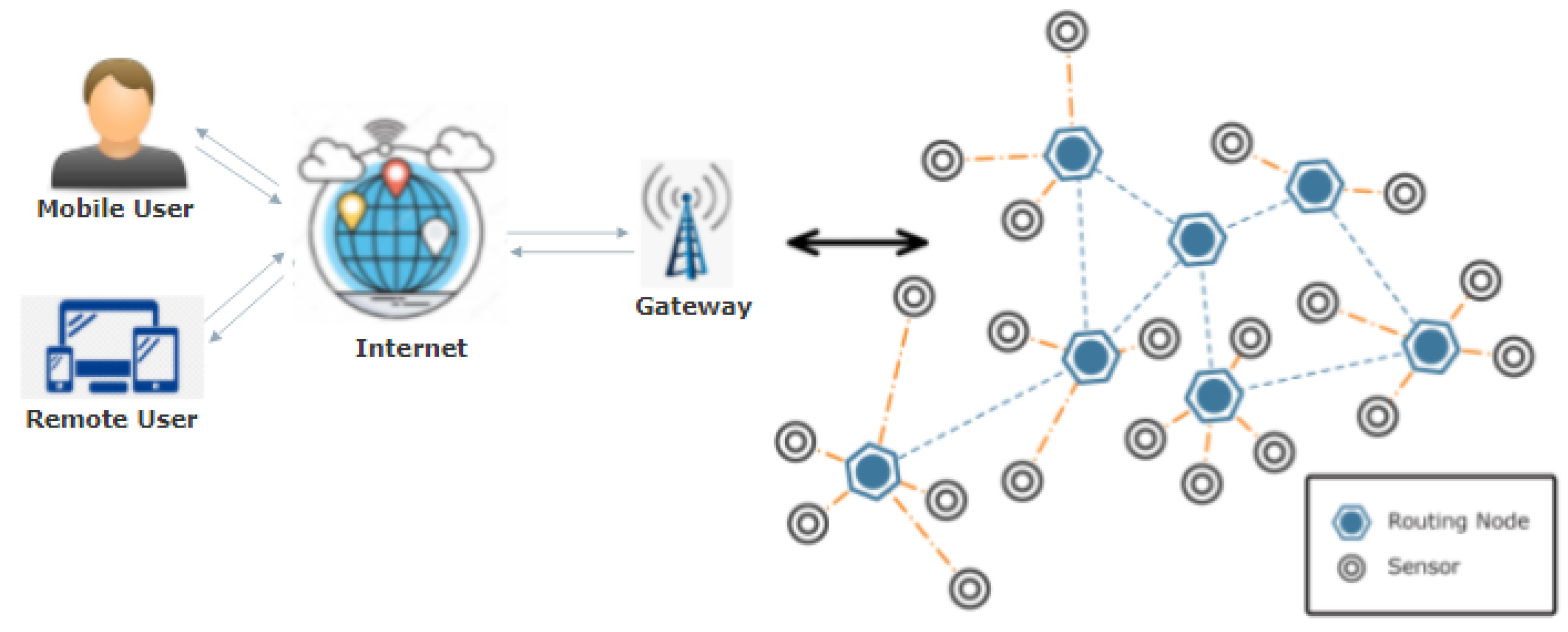
Sensors | Free Full-Text | Applications of Wireless Sensor Networks and Internet of Things Frameworks in the Industry Revolution 4.0: A Systematic Literature Review
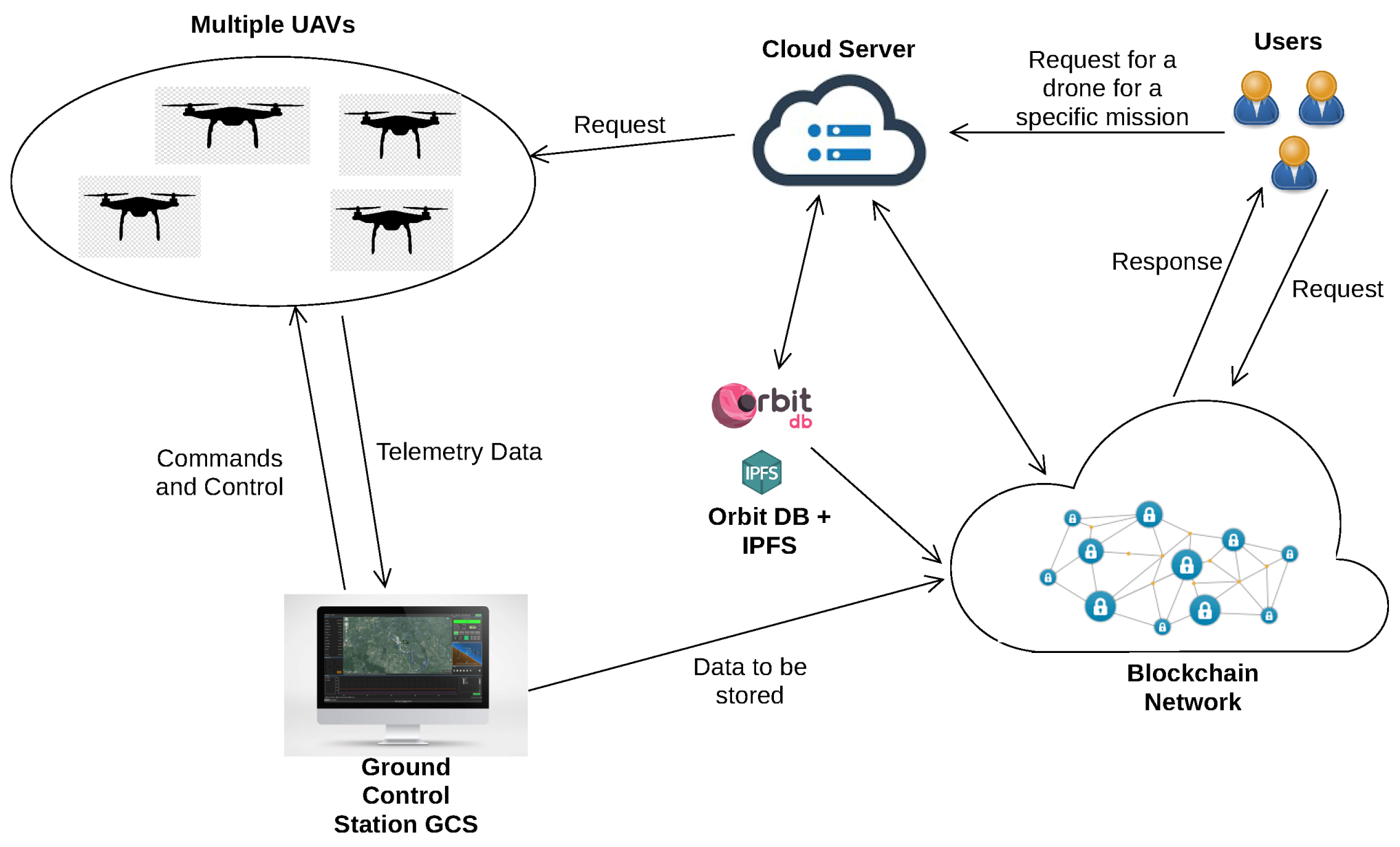
Sensors | Free Full-Text | UTM-Chain: Blockchain-Based Secure Unmanned Traffic Management for Internet of Drones

Throwback Attack: Chinese hackers steal plans for the F-35 fighter in a supply chain heist | Industrial Cybersecurity Pulse | Industrial Cybersecurity Pulse

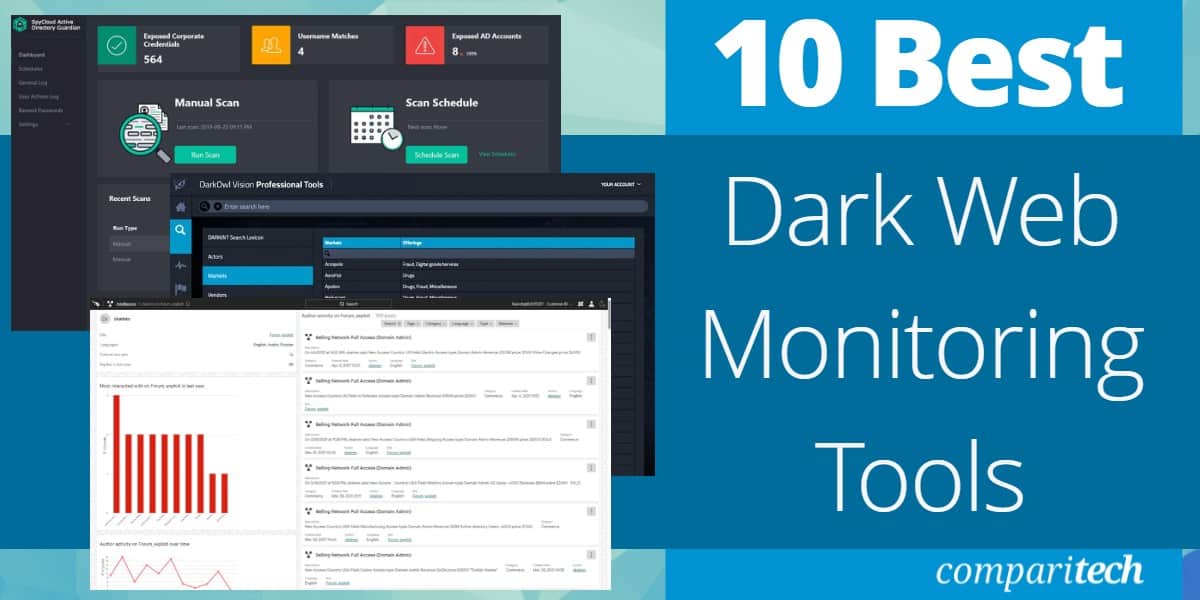
Enterprise data breach: causes, challenges, prevention, and future directions - Cheng - 2017 - WIREs Data Mining and Knowledge Discovery - Wiley Online Library